Draft 27 Nov. 1993, converted to HTML 29 Sep. 1997, updated 2,9,11,13 Jan, 7 Feb 1998. Syntactic update 23 Dec. 1999
 Next chapter: The Internet
Next chapter: The Internet This chapter will be augmented during this course for benefit of others course
participants as well as for outside readers. Contributors will sign their additions.
Background references
are available and are cited when appropriate.
Master on Earth.
Draft 27 Nov. 1993, converted to HTML 29 Sep. 1997, updated 2,9,11,13 Jan, 7 Feb 1998.
Syntactic update 23 Dec. 1999
 Next chapter: The Internet
Next chapter: The Internet
[© New Yorker Magazine]
Traveler, there is no path, paths are made by walking [Antonio Machado]
The purpose of this material is to provide a map to guide the traveler on the emerging information highways. Along these highways nearly the entire world can be reached, so that this guide cannot go very deeply into any specific topic. However, in contrast with more specialized guides, all topics are presented with their interactions and interconnections, so that the traveler can make decision which road to pursue and which off-ramp to use to get into the local neighborhoods and imbued in the local atmosphere.
Highways
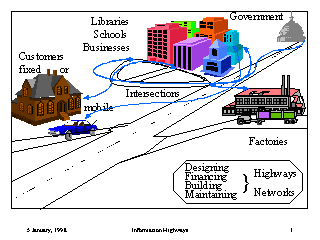
Figure Highways: The Analogy of Transportation and Information Highways (figure on-line).
We will refer to this work as a book, since we are organizing it into chapters. However, crosslinks both with this book and to outside resources will be liberally used. The intent is to have an Internet book, about the Internet, on the Internet, and further exploiting the Internet, as the Internet develops. To accomodate the needed flexibility we will use names for chapters and sections, rather than a traditional, pre-determined numbering.
Since information is an abstract concept, we will use a popular analogy, as shown in Fig. highways. The highways represent the connections, implemented in the digital world by high- and low capacity cables, radio and optical transmissions. Along the nation's highways move people and goods, using a variety of vehicles appropriate to distance, the volume, and size and type of goods. These vehicles and their loads provide the analogy for the data and information to be moved. Armored trucks may be needed to move money securely. Along the highways are our mines, farms, and warehouses. Computer systems similarily collect from data resources and store raw data on their tapes and disks. At intermediate points goods are weighed, inspected, and approved for distribution. Data must often be checked and validated against other observations. Some goods and data can go stale, although spoiled does not smell. Factories take raw materials from multiple sources, combine it with output of other factories, to make products that others will want to buy. Service-oriented computer systems take data from multiple sources, and prepare it for other systems, until it is suitable for information consumers in form and content. The businesses along the on- and off-ramps come in all kind of sizes, and some are likely to be transient, while others are long-lived.
All these activities depend on having adequate highways. The nation's highways are never completed, there is always construction going on. Similarily, we will never be able to design and build the perfect information highways, which means that our data interchanges must be adaptable, so that progress can continue. Periodic traffic jams will also occur, because we will never have perfect building plans, nor the means to execute them all in time. Any analogy has its limits, and we will point out when the limits of the highway and goods analogy are reached.
!!here:scaling to ships, via composition of containers = truck/RR sizes>
To understand one's surroundings when traveling, one needs some sense of history. A fair fraction of this book is concerned with the history of the technology that created todays information highways and the structures that we can enter along them. Every chapter since has a section on History, especially the chapters on the INTERNET for communications and on the supporting UBIquitous computing hardware systems.
Students at Stanford have the advantage of being able to view the Computer History Exhibits, distributed over 6 floors of the Gates building, we plan to put pictures of all exhibited artifacts on the web. Software is harder to display, and here the history sections in the chapters must help.
A great deal of definitional material is provided with the history sections, and many technological concepts are described. The major contribution of this work might well be the technological definitions, which are presented to be both easy to grasp and yet be technically correct.
They are being summarized in a GLOSSARY. Since the definitions always appear in context, the glossary is an important part of this book, which enables its use as a reference work as well. The glossary replaces the traditional index.
REFERENCES to the literature focus on books which provide more detail; with the breadth of material covered a comprehensive bibliography would be extremely voluminous. Keeping up with advances in technology is equally frustrating. We hope to be able to maintain this guide on an electronic library, but current
copyright mechanisms to not provide adequate protection to assure that authors will receive proper fees, as discussed in Chapter SECURITY.
Originally this material was intended to be single-authored book. However, it has been impossible to keep up with the rapid developments on the Internet, the highways are growing faster than the mapmakers can provide the needed guidance.
The plan is hence to use this book as a dynamic resource for teaching, and for documeting what teacher and students have learned in a course. We hope that the layout of the book can survive for some time, while new roads, on-and off-ramps are being built.
The information highways cannot be understood without knowing the organizations who built them, are maintaining them, or depend on them for their operations. We introduce many of them in their contexts, and also index them. Understanding their objectives will help those who wish to cooperate with them, sell their services to them, or purchase services from them.
In the chapters of the book we describe some of the major users of the digital highways. In Sections INTRO.people we introduce tourists and wanderers (Lurkers in [Denning]), people who travel to learn, to experience, and to browse though the the neighborhoods along the highways. Serious researchers will use libraries, subsribe to journals, purchase books, and become authors themselves, as described in Chap. library. Publishers play a critical role at this level. More generally, the new technologies will affect entertainment and education.
Important for the economy are the uses of these technologies in MANUFACTURING, and more general ELECTRONIC COMMERCE. Information is crucial for planning and decision-making. Geographic information has an important role in identifying where one is headed. A topic of concern to most branches of government and individuals is HEALTH care.
The main portion of this book introduces applications for the future information superhighways. Major categories were listed already in the section on< A HREF="#HISTORY">History. The maps and directions in this book indicate then as well what is to found when one takes the off-ramps, and explores the countryside. Since the digital highways are still being built, much local activity has not yet been affected by them, but many businesses located away from the highways are rightfully concerned.
These applications depend on common services. Interspersed with the application chapters we plan chapters dealing with DATABASES that document the past and SIMULATIONS to predict the future. Databases capture the experience of the past and simulations help understand the future. As such these technologies are critical to the goals of the information infrastructure, and support the concept of learning and education wich is crucial to its objectives.
Finally we plan to include material that consider the problems and solutions dealing with the problems of the heterogenity of the world through MEDIATION, the PROGRAMMING and assembly of the software components that are the building blocks of the digital highways and its surroundings, and the SECURITY afforded to travelers and inhabitants.
The initial chapter must focus on the technology of the Internet. And, to finish, we will project the FUTURE with a conclusion.
The greatest joy when traveling is encountering interesting people. People build the institutions, formulate the pathways for interactions, and communicate with a bandwidth not achieved by any electronic method. We present a brief biography in each chapter as a Section a biography. Most of the people are still active, and we hope that they will not take offense at being included.
People are in the end the providers and users of Internet technology and its contents. To understand the fuctions of the Internet we have to recognize the roles that people can play. These roles are not narrowly transcribed, and individuals can assume multiple roles, simultaneously or at different times.
Educated users will also be better be able to make committments, both of their time and their finances. If the book provides the motivation to get involved and learn about the opportunities and eventually exploit them, it has achieved its function.
We have given each chapter (say, X) a similar layout. After a short introduction (Sections X.Intro) we cover the relevant history (Sections X.History) in some detail, as done in general above. We then briefly identify the participants (Sections X.People).
The main body of each chapter (Sections X.Functions) is devoted to the functions that comprise the topic. Many systems provide hundreds of functions, but their essence is captured by a few basic ones. These few will be the focus of the presentation. How more complex functions can be composed out of simple functions will be a secondary concern throughout.
A tertiary class of functions encountered inpractice are meta-functions, those that document, install, or help manage the primary functions. These will only be covered when they are crucial and common, since meta-functions tend to differ widely among system implementatons. In the end, a user of a systems has to be willing to go to a manual provided by the software or hardware vendor. This book cannot serve that particular role.
Since we expect that many people will contribute and modify this work over time we have organized this virtual book into three consistent levels, with a fourth level that is more flexible. This chapter describes the contents, here we summarize the typography for the headers, formatting, and HTML naming conventions.
The technology required to carry out the functions will be discussed in Sections X.technology in a fair amount of detail. In the initial two chapters, the Sections INTRO.Technology and INTERNET.Technology focus on the infrastructure, the highways themselves, and hence are technologically oriented. The technical material presented should suffice for two objectives. First, a reader who needs or wishes to delve further ito the topic is enabled to select and assimilate further specifics. Second, a reader who wishes to use a system embodying the technology, can form an adequate abstract model to to mentally manage its capabilities and its limitations, and become an informed consumer. There is no magic involved in these topics. Furthermore, while the whole composition of the network is indeed complex, it is composed of fairly simple parts. Observe that if systems are not methodically composed of simple parts, they would never work reliably.
For each technology chosen other alternatives are possible. These are presented for the topic of each chapter in a subsequent section X.alternatives. The choice of primary versus alternative approaches i s based on pragmatics: actual use and successes that have been achieved with it. Discussion of alternatives to primary technology broadens the material beyond the purely descriptive information which dominates corrent literature about the Internet.
Often a technology which seemed better has failed to be successful. In many cases we can identify plausible reasons for such failures. We hope that analysis of failures can provide insight in how to avoid similar pitfalls in the future. We should be able to learn more from failures than from successes, since there are more of them, even though less is published about failures than successes. Note that much literature precedes implementations, so that we read much about hoped-for successes that eventually did not pan out.
At the end of each chapter we provide some indication of where the topic is likely to be headed. These are obviously personal assessments, and can easily be invalidated. The book should not be judged by those assessments; giving directions to strangers on a highway is always a risky business, and even more so if the trip will take many years to complete.
Lists are handy as references, but also boring. As Umberto Ecco's protagonist (Sean Connery in the 1986 movie by Annaud) states in the 'Name of the Rose', when trying to identify the villain: "There is nothing more wonderful than a list, and we could go on and on, but now we have to go out and investigate the world">. At the end of a chapter (Section X.lists) we provide a list of the items that the chapter focused on. These lists give a useful summary, but will never be comprehensive.
We introduce now concepts of computing and communication at high level. for readers with experience in computing nothing novel will appear here, but the introduction will assure that all common concepts and terms used later will have been encontered and defined.
A computing systems is layered !see material from s1dbd. reword to use traveling paradigm
 Figure INTRO.layers: Source layers picture from dbd (not yet on-line.
Figure INTRO.layers: Source layers picture from dbd (not yet on-line.
 Figure INTRO.nets (not yet on-line) Users with dumb
terminals, personal computers (periodic
connection) workstations, LANs. WANs (with HPCC), mainframes, mini-computers, databases.
Figure INTRO.nets (not yet on-line) Users with dumb
terminals, personal computers (periodic
connection) workstations, LANs. WANs (with HPCC), mainframes, mini-computers, databases.
! not yet written
modem
 Figure INTRO.communication (not yet on-line):
Linkage from workstations and portables, on analog with modems,
digital phone lines, LANs. WANs
Figure INTRO.communication (not yet on-line):
Linkage from workstations and portables, on analog with modems,
digital phone lines, LANs. WANs
Operating systems control the computer hardware. The five major functions being provided by an operating system all are related to resource alloaction, namely figuring out who gets to use what part of the computer when. We also indicate the metrics used for the five functions.
We will not further present the technology of operating systems, but note that types of operating system are strongly related to the management mode of a computer system and its enviroment. That topic is exOApanded on in a Chapter on Ubiquitous Computing. A programmer, trying to make the hardware something the novel, may want to change the operating system. But in a computer serving many people any change that improves the system for some is likely to hurt others, at least until changes settle down. This means that few people, often labelled * superusers, have the priviledge of changing operating systems. But if you operate your machine, then you can be your own superuser; you can only hurt yourself.
Other people see the hardware and the operationg system as a whole. If different types of computers have the same operating system they may act nearly identical, if the operating systems on the same machine is replaced, it may change so radically that no prior work is usable.
Since this first chapter does not cover a specific technology or application area, it is not clear what the alternative to an introduction are.
There are of course many alternatives to learning about the web. All of them should involve actual use, but there is more material being added daily then any sigle person can read, so that any book should supply directions and a roadmap.
The concept of directions: How to find something and having a roadmap, which gives one the abilty to select one's own path are alternatives as well. This book is intended to be more of a roadmap then a set of directions to follow when traveling on the information highway.
For readers who start reading the conclusion of a chapter and the proceed forwards, let us remind them that this to be a work of many authors, since the highways, and hence the maps to it can never be complete,
Even though this book provides a fairly high-level overview, many technical topics are introduced, topics that at one time were far beyond the interest and need of most individuals. In the early 1960, when computer used was in its infancy, but growing rapidly, extrapolations of the growth in the programming profession indicated that by 1995 there would be as many programmers in the United States as adults. That extrapolation was viewed as clearly ridiculous, what about all the other professions? In retrospect, the prediction has become true, but not in sense seen in in 1965. Anyone who uses a spreadsheet is a programmer, maniging such computations required specialist expertise in the 1960ties. Even obtaining information from the web initiates operations that once were so complex that they could be performed only by information system analysts. The use of word-processors, VCRs, even microwave ovens involves instructing computers what to do. It won't be long before most of us will be information scientists as well.
The purpose of obtaining information is to help us make better decisions. having information enables us to make the best choices, weighing benefits, costs, and risks. Balancing these factors remains a human !task, since the valuation of dissimilar factors cannot be automated. Only when values are assigned to the factors presented for the alternatives can we delegate the making of decisions to a computer. In a recent survey 85% of the people queried felt that they did not need more information.. When we use the abstract term * decision maker we are likely to think of captains of industry, of generals, or of millionaire investors. But in practice we are all decsion makers, in selecting purchases, in balancing work and health, when planning vacations, or switching among television channels. For information to be relevant however we must have choices, in goods to be purchased, in selecting sports and healthcare choices, in destinations for travel, and in entertainment. There is hence an interplay between having a free society and liing in an information society.
Since using computers beneficially is the prime motivation for establishing the information highways we will start the biographies with a brief history of a person who always focused on his profession, Genetics, but in the process used and motivated computing and communication facilities. Professor Joshua Lederberg !BACKGROUND>. !get his Nobel lecture>. In 19!xx> he assumed the post of professor and chairman of the Stanford Department of Genetics, !shorlly after it, and the entire Medical school moved from San Francisco to the main campus near Palo Alto, in order to achive closer cooperation with the science departments of Stanford University. In 1964 a computer science department was established at Stanford, led by Prof. George Forsythe. New faculty members, Profs. John McCarthy, the inventor of the language LISP, used widely for applications in Artificial Intelligence (AI), and Prof. Edward Feigenbaum, whose prior work was in Cognition, another topic in AI, were especially relevant to Prof. Lederberg's interest. !what then> for In 1964 he started using one of the largest computers in the U.S. over a remote phone line between Northern and Southern California. The * IBM AN-FSQ32 was designed to control the Air Defense System of the U.S., but was never actually placed into service. However, computer specialists at System Development Corporation (SDC) installed a * LISP system on that machine, and its large memory (xxK) permitted larger programs to be run than on computers available at Stanford University. !led to xxx machine at Livermore , an early supercomputer > !* ACME> !* SUMEX-AIM> !email article> !Rockefeller University> !* Collabratories> !recent>.
!Clark Weissman was working on Adept in 360 pr !contact Kameny> >
This list was last updated in 1995. It has grown manyfold since. In addition to adding more services, we also need better descriptions of the services being added, and their value. Organizations providing network services are listed in Chap. INTERNET.Networks.
| name | sponsor | technology | charging | services | [ref] | | | |||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| AOL | America Online / Vienna VA | private network | bboards, email, shopping, NY Times | fixed base fee, 600 000 subscribers feb94 | | | ||||||||||||||||||||||||||||||||||||
| ARPAnet | DARPA, DoD, Washington DC | the original packet network | telnet, ftp, email | | | |||||||||||||||||||||||||||||||||||||
| COMPUSERVE | Compuserve | H&R Block | 2M subcribers (Feb94) | bboards, stock quotes, airline schedules, email | | | ||||||||||||||||||||||||||||||||||||
| Delphi | News Corp., NYC | stock quotes, enccyclopedia | Internet access | info@delphi.com | | | ||||||||||||||||||||||||||||||||||||
| eWorld | Apple / Cupertino CA | shopping, bboards, ...? | discontinued | | | |||||||||||||||||||||||||||||||||||||
| FrEDMail | FrEDmail foundATION/ Bonita | Internet access for students | | | ||||||||||||||||||||||||||||||||||||||
| Genie | General Electric / | | | |||||||||||||||||||||||||||||||||||||||
| In Touch | IBM / | proposed corporate intel | | | ||||||||||||||||||||||||||||||||||||||
| MNI | Motorola Inc/ <>|
proposed intelligent, mobile voice messaging | |
| NSFnet | NSF, Washington DC | [John Clement@NSF]
| funding agent, taxes | |
| NetCom | NetCom Inc. | commercial access provider | subscription |
telnet, ISP | |
| PersonaLink | AT&T |
proposed intelligent messaging, browsing, shopping | |
| Prodigy | IBM and Sears/ |
shopping, cable TV interaction | |
| WELL | Whole Earth 'Lectronic Link/ Sausalito CA |
ISP / collaboration group support | membership fee and usage charge | | |
| |
| term | explanation | details | |
|---|---|---|---|
| bboards: | bulletin boards | | | |
| chat: | interactive, group messaging | | | |
| email: | electronic mail | | | |
| ftp: | file transfer to load user's computers | | | |
| intel: | intelligent messaging | | | |
| interop: | Internet Service Providers. | ||
| muds: | fantasy worlds| | ||
| telnet: | remote login to other computers | | |
Infrastructure and technical support are listed in Chap.INTERNET.lists.
| number | Title | Web pointer | Maintainer | Status | | |
|---|---|---|---|---|---|
| 1 | Introduction | intro.html | Gio | draft, available, use for CS99 W97/98 | | |
| 2 | The Internet | internet.html | Gio | draft, available for CS99 W97/98 | | |
| 3 | Ubiquitous Computing | ubi.html | Gio | draft available, to cover computing infrastructure | | |
| 4 | Information Services | wais.html | Gio | incomplete, on-line, to cover browsers etc | | |
| 5 | Entertainment and Education | entedu.html | Gio | incomplete draft, on-line, due for CS99 W97/98 | | |
| 6 | Libraries | library.html | Gio | draft, on-line, due for CS99 W97/98 | | |
| 7 | Health Care | health.html | Gio | incomplete draft, on-line, due for CS99 W97/98 | | |
| 8 | Electronic Commerce | E-com.html | Gio | outline only, on-line | | |
| 9 | Manufacturing | manuf.html | Gio | incomplete draft, off-line | | |
| 10 | Planning and Decision-Making | plan.html | Gio | planned | | |
| 11 | Databases | db.html | Gio | planned, their services and integration | | |
| 12 | Simulations | sim.html | Gio | planned, their services and integration | | |
| 13 | Mediators | mediators.html | Gio | draft available. How to deal with heterogeneity | | |
| 14 | Security | security.html | Gio | draft, available online | | |
| 15 | Future Directions | future.html | Gio | draft, to be used on CS99I 97/98 | | |
| R | References | refs.html | Gio | initial version available for CS99I 97/98 | | |
| G | Glossary | glossary.html | Gio | initial version available for CS99I 97/98 | | |
| H | HTML brief | html-inf.html | Gio | prepared for CS99I 97/98 | | |
 Next chapter: The Internet
Next chapter: The Internet
o List of all
Chapters.
List of all
Chapters.
CS99I  CS99I home page.
CS99I home page.